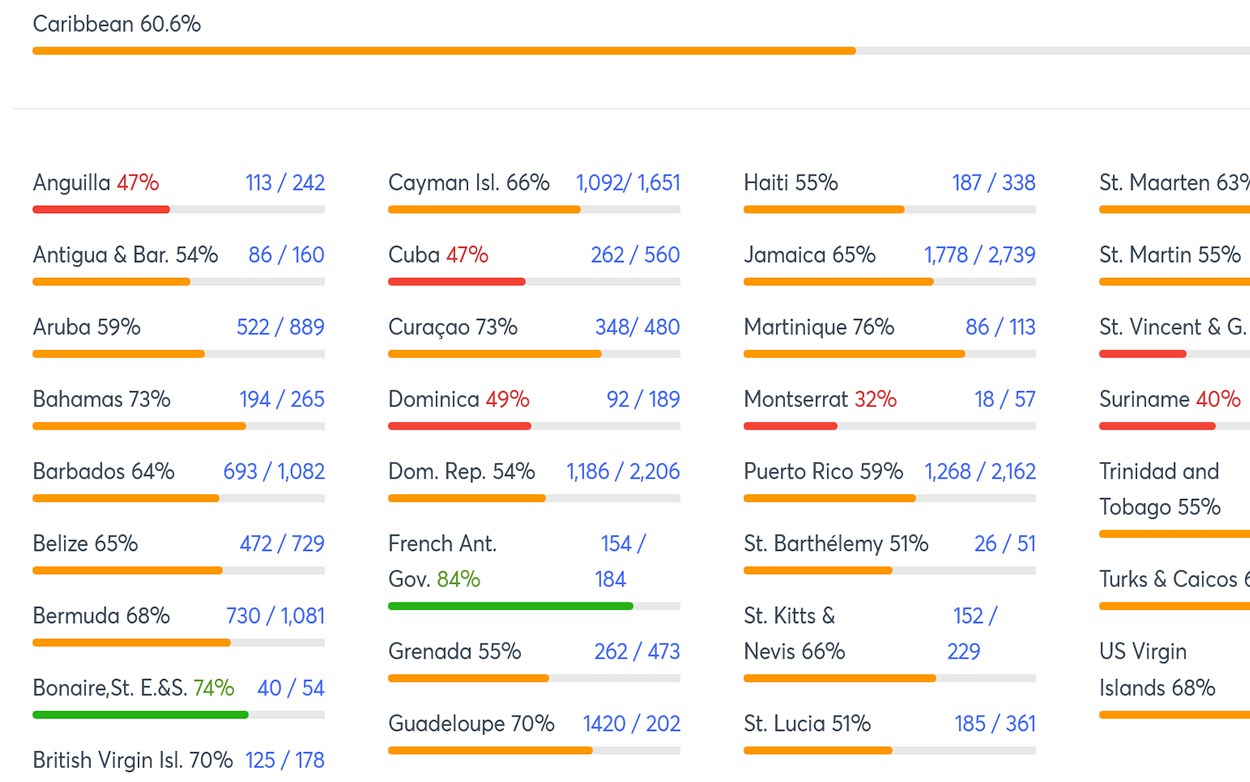
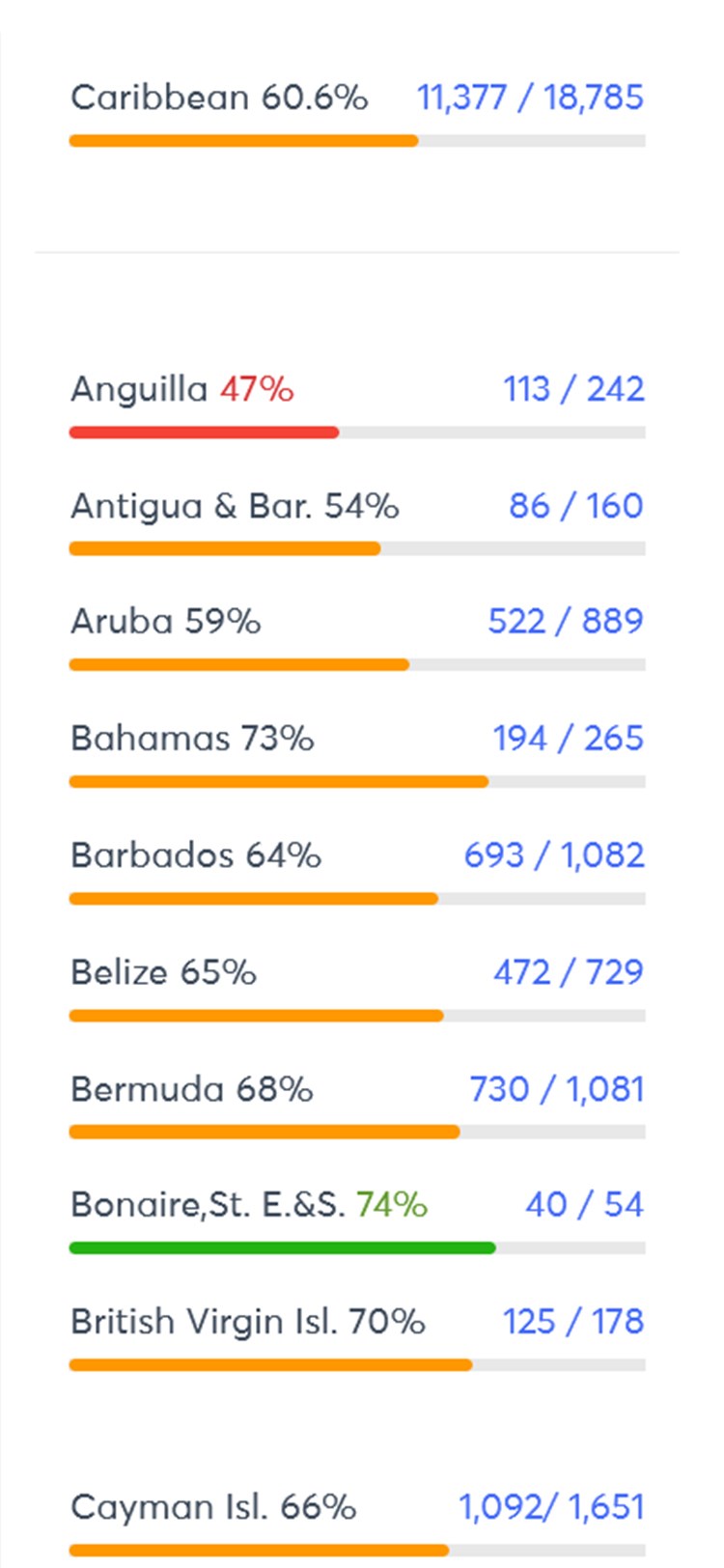
Vulnerability Scanning Services
Scan all systems on the network for security vulnerabilities.
-
Identify security vulnerabilities without the risk of exploits.
-
Understand the potential of identified vulnerabilities how much damage they can do.
-
Get a report suitable for both your management and technical teams.