CIS Critical Controls Compliance Assessment Services
Measure your organisation's compliance with CIS Critical Controls.
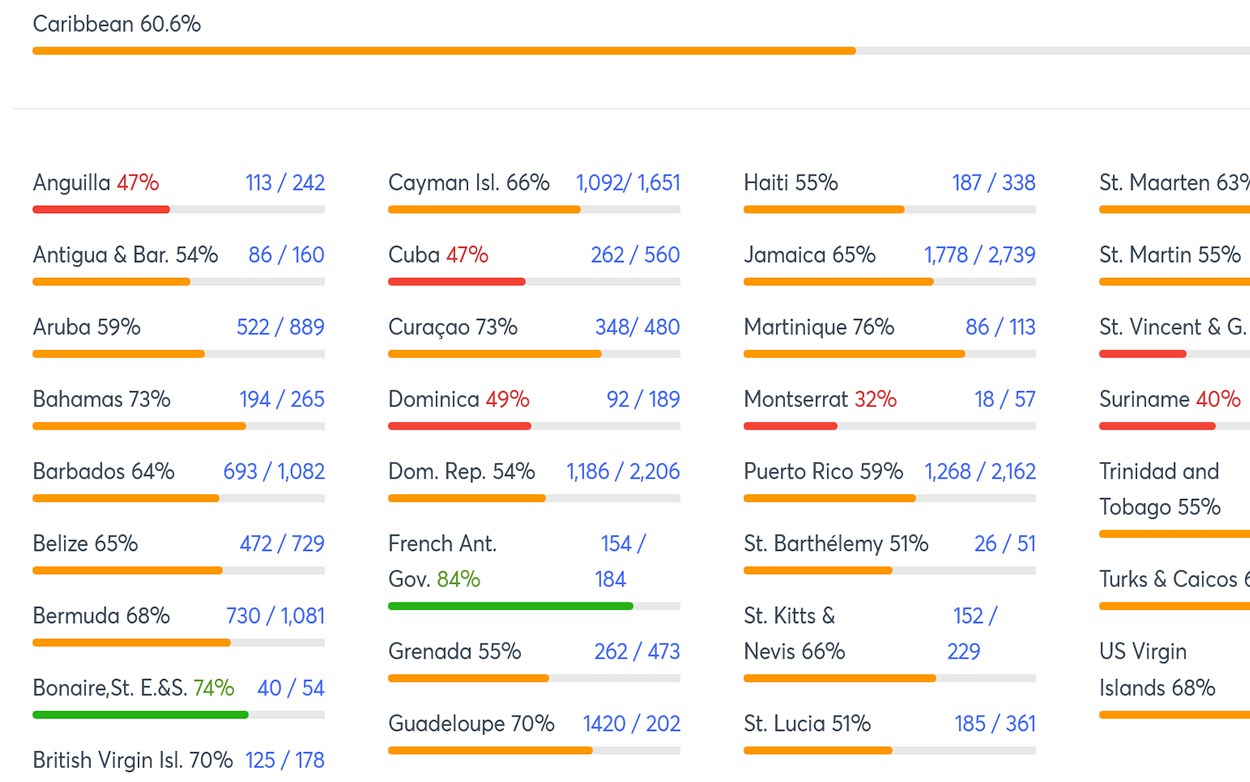
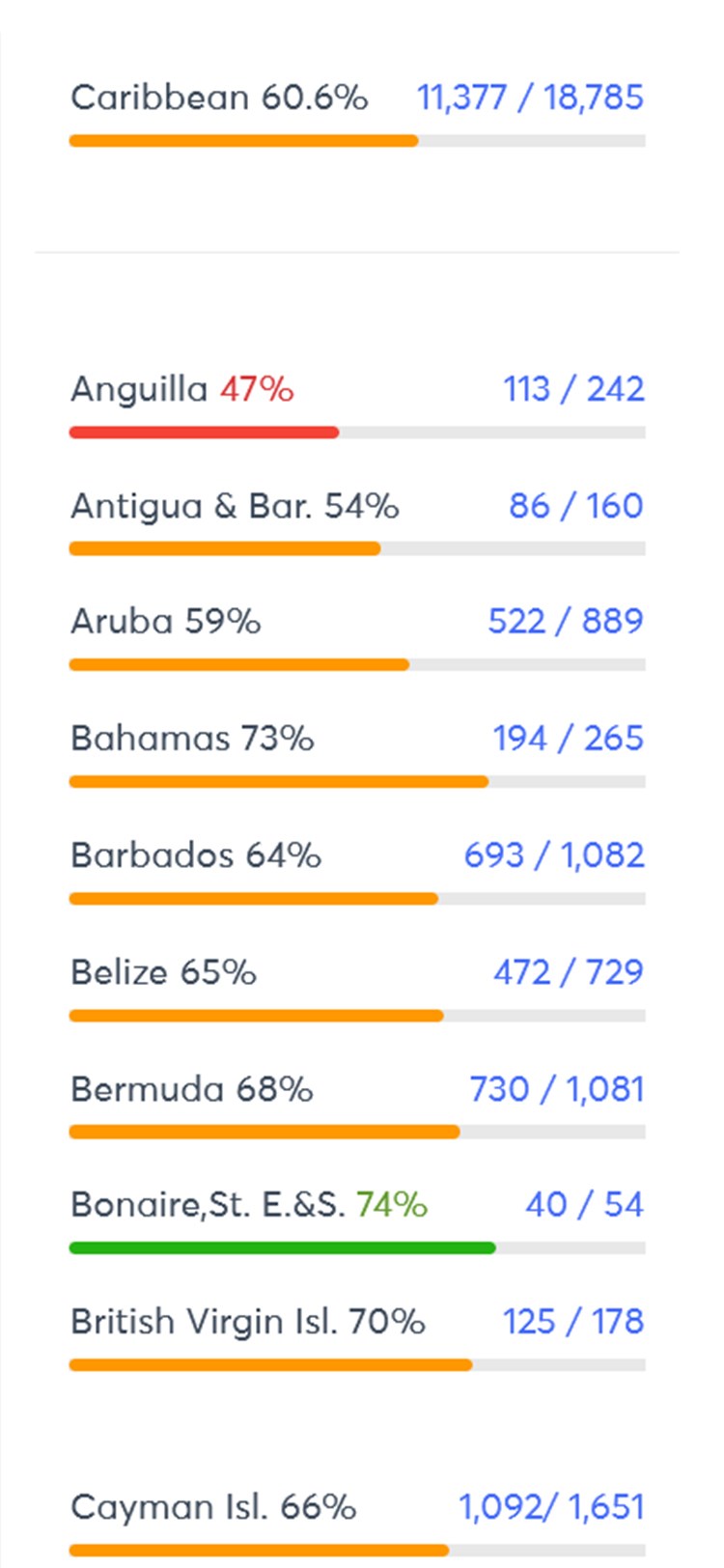
CIS Critical Controls is an internationally recognised set of prioritised actions to protect your organisation and data from known cyber attack vectors.
-
Identify missing gaps.
-
Implement missing controls.
-
Get guidance to stay compliant.